Website security is among the biggest challenges that web professionals face. It’s a constant battle to thwart malicious actors. Great effort is required. Yet the results aren’t encouraging.
Those of us who work with WordPress can empathize. The content management system’s (CMS) popularity makes for a tempting target. A deluge of automated attacks is sure to hit every installation.
It has also become clear that there are no bulletproof solutions. Security plugins that scan for malicious files aren’t perfect. They might miss an infected file. And some malware can elude detection.
It’s a reality check for web professionals. Taking proactive steps is a positive thing. But it could create a false sense of confidence. Eventually, you find yourself cleaning up after a successful attack.
Determining the cause of an attack can be difficult. That makes it harder to prevent the next one.
There is an often overlooked tool that can help, however. Tracking backend activity in the WordPress dashboard provides crucial information. And it may save you from a headache or two.
Keeping Track of Who Does What
WordPress websites require maintenance. Plugins, themes, and the core software should be updated as needed. Making frequent site backups is also recommended. But we can go deeper.
Activity tracking provides a different perspective on your website. And it’s not just for detecting intrusions.
Administrators can identify potential workflow issues. And it helps for troubleshooting a “broken” page or undesirable content change.
You can see all manner of information. For example, when a user logs in and updates a page. Or pinpoint when a plugin was installed or deactivated.
And that’s not all. Depending on the activity logging plugin used, you can track the following:
- Content creation, edits, or deletions;
- Failed login attempts;
- Password reset attempts;
- Plugin installation, activation, and deactivation;
- Updates applied to WordPress;
- User creation and deletion;
These actions could be typical user behavior. But they might also be a sign of something more sinister. Reviewing this data will help you confirm what happened.
Note that this data won’t likely tell you how your website was compromised. But it will tell you what actions an attacker took while logged in.
Log Dashboard Activity with a WordPress Plugin
There are several plugins available that track dashboard activity. Security suites like Wordfence and Solid Security (formerly iThemes Security) include some form of this capability.
For this example, we’ll use a niche plugin called Simple History. It’s free and tracks a wide array of activities by default. It also works with popular plugins like Jetpack and Advanced Custom Fields. There’s also an API for logging custom events.
Even better is that Simple History doesn’t require much setup. Install the plugin, activate it, and it just works. A widget will now display on the Home screen. You can see a more detailed log by visiting Dashboard > Simple History.
In addition, the plugin can optionally create an RSS feed. That lets you keep track of activity without having to log in.
Here are a few examples of how the plugin can boost security:
Track User Logins
Simple History will record when a user logs into your site. It will also report any actions the user took.
There are a lot of reasons why this data is helpful. For example, it can help you identify a compromised account.
The plugin provides a timestamp and the user’s IP address. If either of these items looks suspicious, you can take further action. You could then reset the user’s password and alert them to the issue.
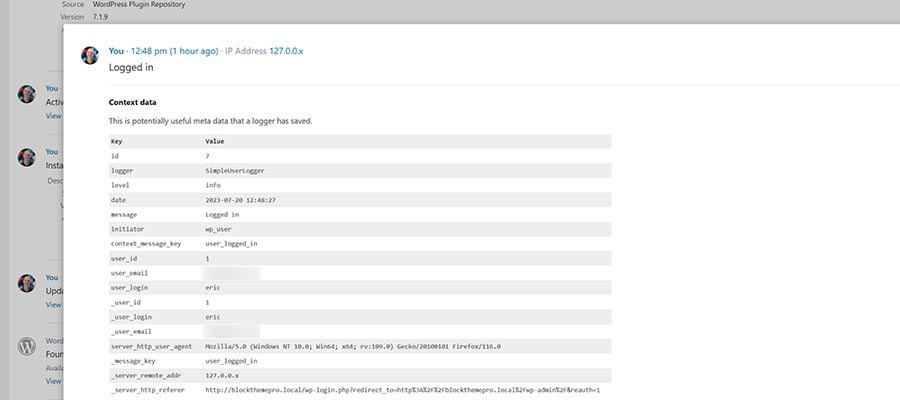
Simple History provides details of user logins.
Find the Origins of a Suspicious User
It’s important to know who has access to your website. WordPress has several user roles – administrator being the highest. An administrator can perform potentially-damaging tasks. It could be catastrophic in the wrong hands.
Take note if you see that an unfamiliar administrative account has been created. It could mean that a malicious actor has gained access.
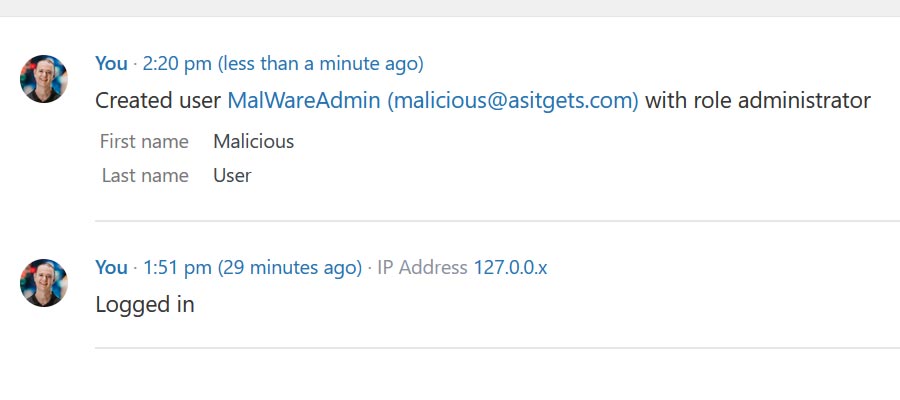
A suspicious user was created. Is it a sign of a compromised website?
How Did That Plugin Get Here?
Website administrators also need to keep track of installed plugins. But new plugins can go undetected. You can use activity logging to find out who installed a plugin and when they did it.
Pay close attention to plugins that have known vulnerabilities. Or those that enable file uploads or running code within the back end.
A malicious actor may install a plugin to take advantage of an exploit. They can use it to install malware, for instance.

Attackers may install plugins to help infect your website with malware.
Be Informed about Content Changes
Websites with multiple authors can get messy. It can be difficult to track changes to content. But knowing what’s changed has security implications.
For example, SEO spam is a popular type of attack. The attack adds hidden content to existing pages and posts. It may also contain redirects to malicious websites.
Simple History logs content changes. You’ll see who made changes, along with when.
The plugin also taps into the WordPress revisions feature. That provides a highlighted view of each change.
This tool may not catch every vector of attack. But it’s another way to stay on top of your content.
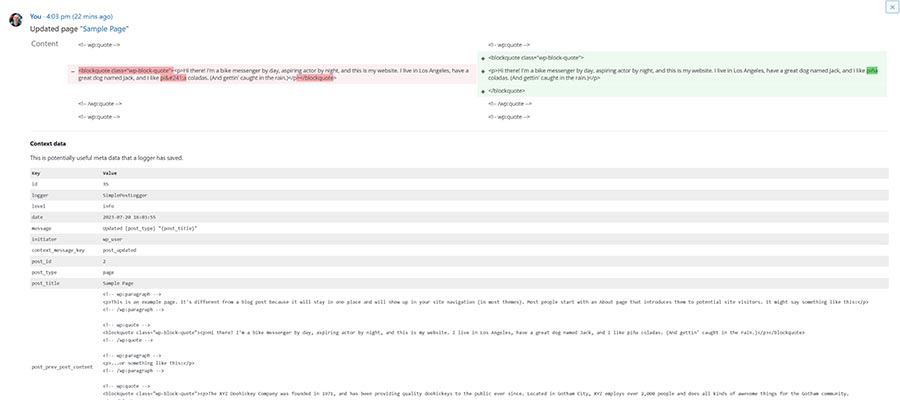
Simple History helps you see what content was changed and when it took place.
The More You Know
As it turns out, installing a WordPress security plugin isn’t enough. Your website still runs the risk of being compromised. Indeed, security is a 24/7 responsibility.
That’s why having backend activity data on hand is so important. Sure, it may help you clean up a hacked site. But it may also help you catch suspicious activity before it’s too late.
At the very least, you’ll have a list of user actions. It will come in handy if/when an incident occurs.
It’s just another proactive step we can take to stay safe. And it requires minimal effort. What’s not to love?